Previously, on "Weekend Projects for Homelab Admins With Control Issues," we created our own dynamically updating DNS and DHCP setup with bind and dhcpd. We laughed. We cried. We hurled. Bonds were forged, never to be broken. And I hope we all took a little something special away from the journey—namely, a dynamically updating DNS and DHCP setup. Which we're now going to put to use!
If you're joining us fresh, without having gone through the previous part and wanting to follow this tutorial, howdy! There might be some parts that are more difficult to complete without a local instance of bind (or other authoritative resolver compatible with nsupdate). We'll talk more about this when we get there, but just know that if you want to pause and go do part one first, you may have an easier time following along.
The quick version: A LetsEncrypt of our own
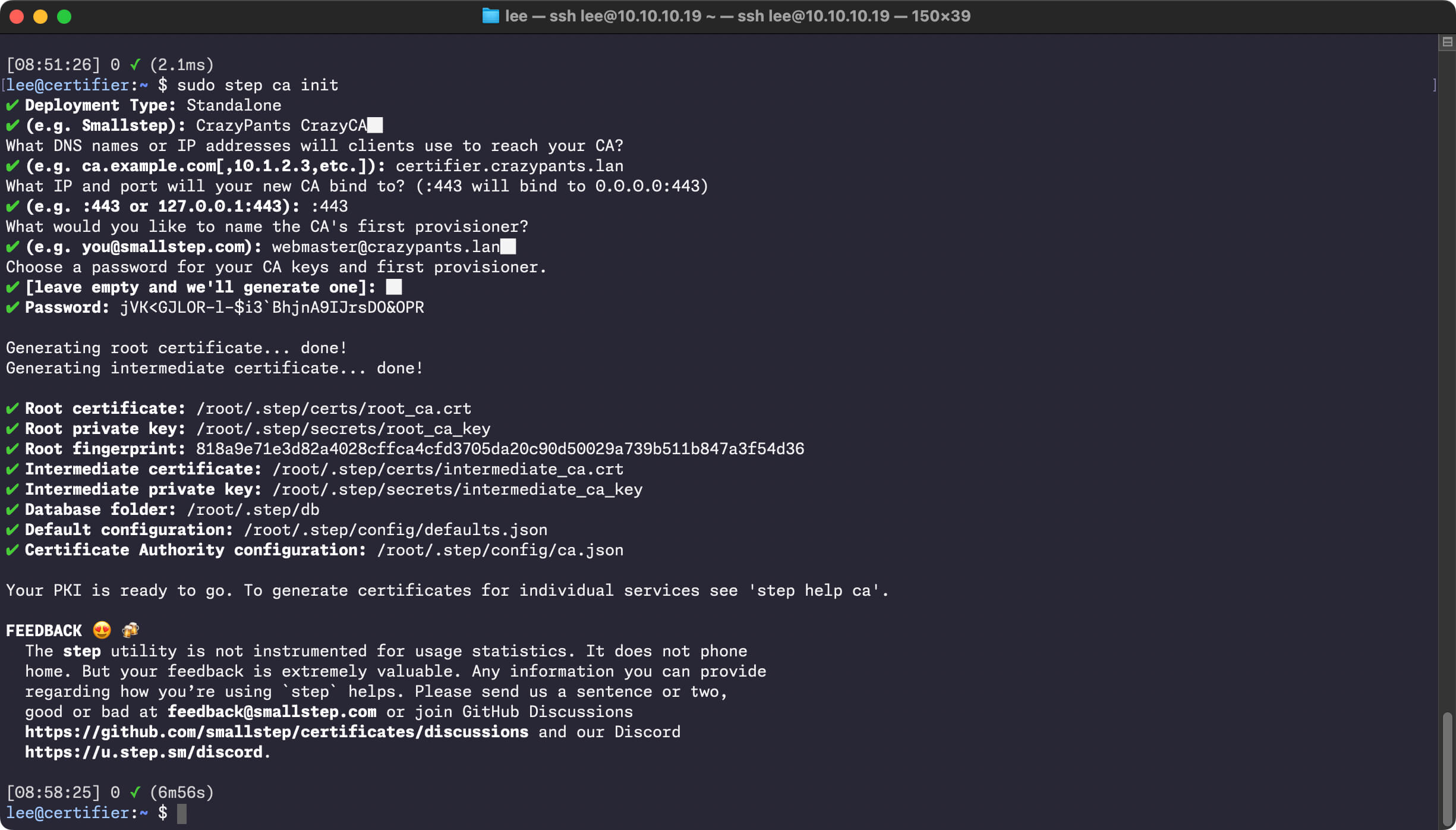
This article will walk through the process of installing step-ca, a standalone certificate authority-in-a-box. We'll then configure step-ca with an ACME provisioner—that's Automatic Certificate Management Environment, the technology that underpins LetsEncrypt and facilitates the automatic provisioning, renewal, and revocation of SSL/TLS certificates.
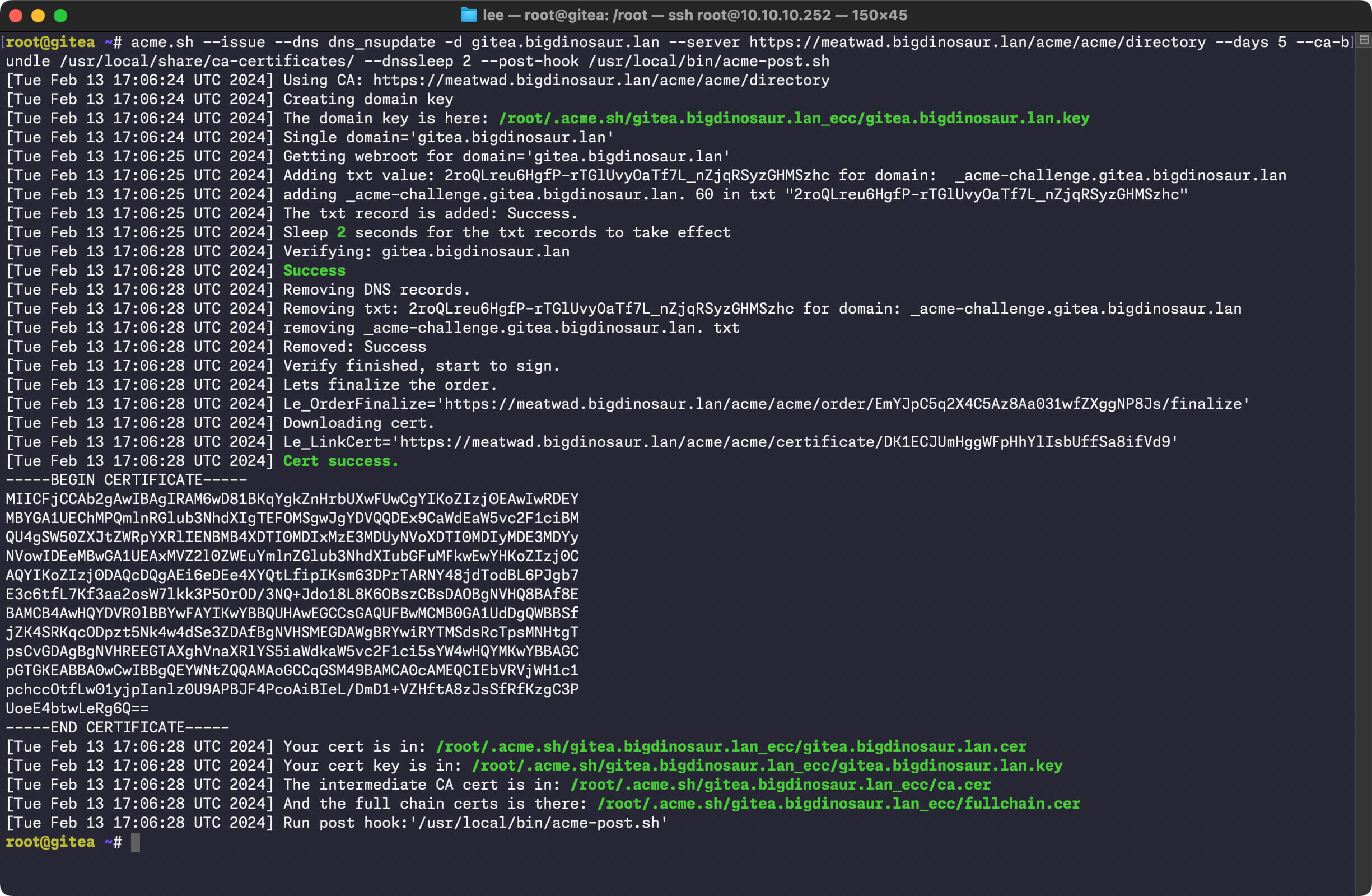
After we get step-ca listening for incoming ACME requests, we'll talk through the ways to get the self-hosted services on your LAN-speaking ACME so they can start automatically requesting certificates from our step-ca certificate authority—just like how LetsEncrypt works.
I'll focus exclusively on using acme.sh for requesting and renewing certs on clients because it's the tool I'm most familiar with. But everything we do should be doable with any ACME client, so if you're more comfy with certbot or dehydrated whatever, feel free to use that on your clients. The instructions should be pretty easy to adapt.



 Loading comments...
Loading comments...
